Secret sharer v3: Initializing and running tests
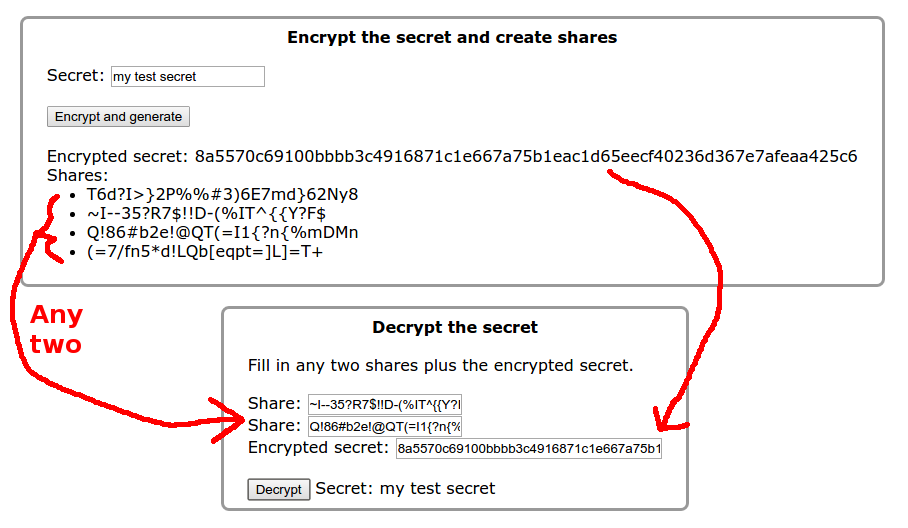
This tool is for dividing a secret among up to four trusted people such that anyone one person knows nothing about the secret and any two people can reconstruct the secret. As an example use case, suppose you use a password manager and worry about forgetting your master password. Using this tool with four family members would make it so that any two family members could reconstruct the master password if you forget, but your master password is safe from one of them accidentally posting their share of the secret on the internet. See below for usage and details.Secret:
Fill in any two shares plus the encrypted secret.
Share:
Share:
Encrypted secret:
How to use
- Wait for the top of this page to say "Ready" (it runs some self-tests first).
- Type a secret into the first box below and press "Encrypt and generate".
The tool encrypts the secret and also displays four "shares". Any one share reveals nothing about the secret, and any two shares are adeuate to decrypt the secret.
Note: This tool runs in your browser and does not use the network except for Google analytics. You can just trust me, read the javascript source for this page and verify it yourself, or browse "in-cognito" with wifi disabled.
- Pass one share to each trusted person. Whoever will be reconstructing the secret will need the encrypted secret. You could send the encrypted secret to all four people. I recommend having them keep the encrypted secret in a safe place separate from their share.
... and then later when you want to recover the secret....
- Enter the shares from any two people into the "Decrypt the secret" area, below. In addition, enter the encrypted secret and press "Decrypt". The tool will show the original secret.
Note: Secret sharing and cryptography is tricky stuff and many smart people have made mistakes implementing it, perhaps including myself. Take care if you use this for anything critical. Also, the security of a given cryptography algorithm weakens over time as computers get faster and more smart people find new ways of attacking it. So it's probably a good idea to reexamine the encrypted secret every few years and see if, for example, AES-128 is still considered decent encryption.
See my blogpost for info on how this tool works and to leave comments. The short version is that it uses Shamir's scheme for secret sharing over a finite field based on the prime 2^128-159 and encrypts the secret with AES-128 using a random 128-bit key.